| Michael Horowitz |
Home => Windows Update vs. my Router
|
| Michael Horowitz |
Home => Windows Update vs. my Router
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
If you are techie, this should be an interesting story.
Once upon a time, someone who works for a very large company was working from home connected to a Pepwave Surf SOHO router that I had configured. For many months, all was well. Eventually the employee noticed that Windows 10 was not getting updates.
I did not think the router was a suspect, because, like every large company, the at-home employee connected to their corporate VPN first thing. My experience with consumer VPNs is that all the bits and bytes flow to/from the computer, through the VPN connection/tunnel, and the router is oblivious to it all. All the router sees is a single encrypted connection to the VPN server and the router can not see into the encrypted data.
The work-at-home employee brought this to the attention of their corporate tech support department and the techie downloaded Windows 10 service pack 1909 and installed it. At the time 1909 was fairly new, but it was the only thing installed, there were no subsequent updates. As this did not address the real problem, a few months later the lack of Windows 10 updates again became an issue. What was going on?
There are many types of VPNs and each type has assorted configuration options. One option is called split-tunneling. A tunnel is the official term for the VPN connection, and split-tunneling means that some data travels through the encrypted VPN connection and some data does not. I have seen this as an option on some consumer VPNs (Tunnelbear calls it SplitBear) but never bothered with it.
Could it be that the requests Windows uses to check for updates were not going through the VPN and thus were at the mercy of the many defenses built into the router?
That's hard to tell, but the Surf SOHO can easily show if the VPN is using split-tunneling or not. It does this by displaying every connection that a device has to a computer on the Internet. A sample of what this report looks like is shown below. In this case, the device at IP address 192.168.1.184 has five connections that are using SSL on port 443 and two connections using HTTP and port 80. If it was using a VPN without split-tunneling, all the router would see would be one connection to the VPN server.
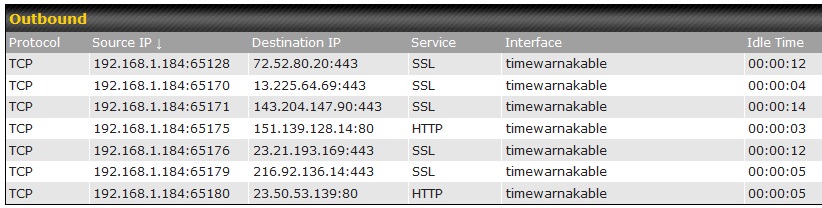
Taking a detailed look at the non-updating Windows 10 device with the router, showed that it had many different connections to assorted computers on the Internet, proving that all data was not going through the corporate VPN. The router was now a suspect.
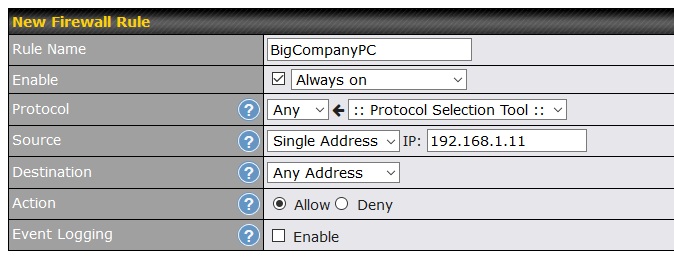
The first thing I looked at were the outgoing firewall rules (Advanced tab --> Access Rules). The router had quite a few, so I carved out an exception for the corporate computer. As shown below, I created a new firewall rule that allows any traffic from the corporate computer (IP address 192.168.1.11) to leave the router. No blocking. No logging. Firewall rules are evaluated from top to bottom and this was the first rule on the top.
End of story, or so I thought.
Months later, when there were still no bug fixes, it was back to the drawing board.
This time I looked at Web Blocking, the blocking of domains accessed with HTTP and HTTPS. Here again, the router was blocking tons of domains (a sample is below) and I did not want to un-block them for all the other devices connected to the router. So, another carved out exception.
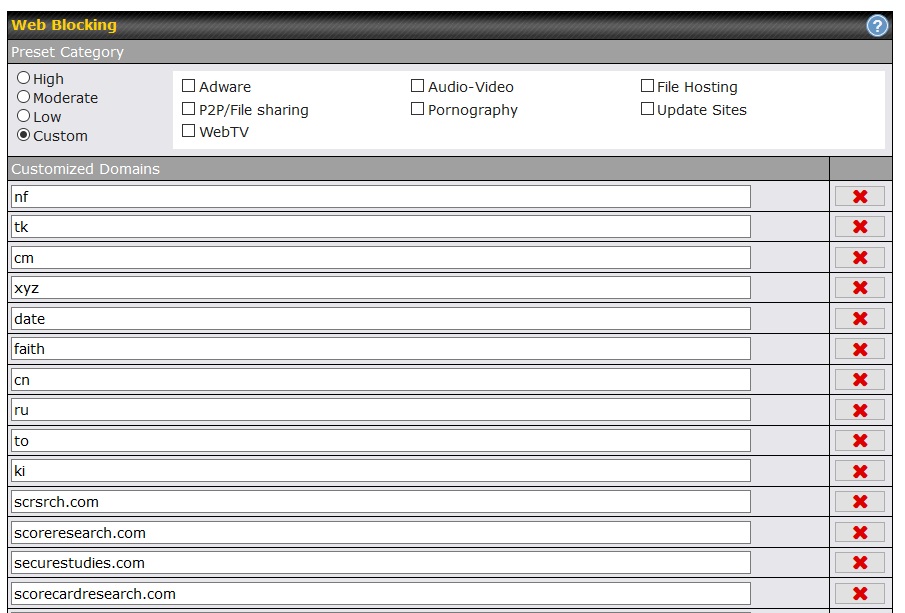
The great thing about the Peplink Web Blocking feature is the wildcard way it works. For example, if you ask it to block yahoo.com, it will also block mail.yahoo.com and sports.yahoo.com and news.yahoo.com and anything.else.yahoo.com. Often people mis-type ".com" in a URL as ".cm" which has led to a assorted typo-squatting with bad guys registering ".cm" domains for malicious purposes. Ask Web Blocking to block "cm" (seen in the screen shot above) and it blocks every domain that ends with ".cm".
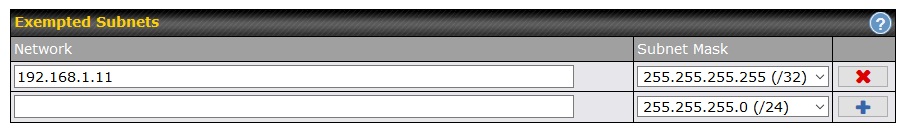
To make exceptions (white list, if you will) Web Blocking lets you exempt subnets. What the router interface and the manual do not say, is that a subnet can be as small as a single computer. You just need to understand subnet masking. As shown below, the corporate computer (IP address 192.168.1.11) was now exempted from Web Blocked domains.
FYI: I later had to carve out another exception to the Web Blocking rules when a ROKU box attached to the router would not play any YouTube videos.
Again, I thought I was done.
But, still no bug fixes for Windows 10. Ugh.
I was tempted to blame Microsoft at this point. Previous research (more below) showed me just how complicated the Windows Update process is on Windows 10. Lots of programs, services and scheduled tasks. Lots. And, it constantly changes. Still, I went back to the router one more time.
The last defense in the router was DNS.
To back up for a second, DNS is changing. Old school, legacy DNS is not encrypted. The newer DNS, offered by DoH and DoT, is encrypted and thus will bypass the DNS in the the router, much as a VPN and TOR do. Windows 10 does not yet support encrypted DNS. When it does, outgoing firewall rules will be a very interesting topic. But, the discussion here is about legacy DNS.
All the devices connected to this particular Surf SOHO are forced to use the router for their DNS. This is an optional (and great) feature of Peplink routers. Kids can not bypass family-friendly DNS servers by hard coding other DNS servers into their computing devices. The router rules :-)
DNS can be used for blocking by simply assigning the thing you want to block to an invalid IP address, such as 0.0.0.0. You do this with Peplink routers at Network --> Network Settings -> Local DNS Records. Below is a screen shot of what this looks like.
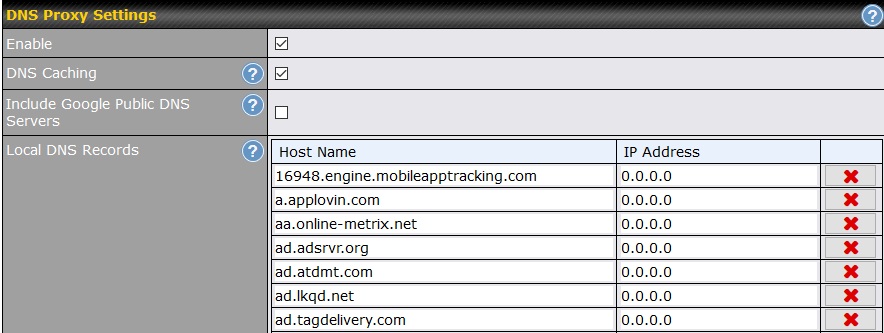
The disadvantage of DNS is that it blocks one computer at a time. It can not block facebook.com the way Web Blocking does. With DNS you have to block abc.facebook.com and def.facebook.com and anything.you.want.facebook.com individually. The advantage is that the blocking is total. Web Blocking only blocks HTTP and HTTPS. DNS blocks all protocols.
The router was using DNS to block a pretty long list of specific computers. Which, if any, were preventing Windows 10 from learning about available patches? I took an educated guess and moved the following DNS names over to Web Blocking (which already had an exception carved out for the corporate computer).
NOTE: There were actually two different prod.do.dsp.mp.microsoft.com computers being blocked by DNS. Think of them as thing1.prod.do.dsp.mp.microsoft.com and thing2.prod.do.dsp.mp.microsoft.com. I combined them into one Web Blocking rule.
|
prod.do.dsp.mp.microsoft.com settings-win.data.microsoft.com sls.update.microsoft.com watson.telemetry.microsoft.com ctldl.windowsupdate.com |
| These five domains/subdomains can block Windows Update |
BINGO!
With access restored to the above five domains/subdomains, Windows 10 finally learned about and installed a large number of updates.
Whew.
Not forcing microsoft.com and windowsupdate.com to use the corporate VPN sure seems like an oversight to me.
But, [sarcasm] who am I to question the techies at a company with over 100,000 employees? [ /sarcasm ]
Do all five domains/subdomains need to be blocked to prevent Windows 10 from updating itself? I don't know.
IRONY
I have been looking at blocking Windows Update on Windows 10 for a long time. Back in January 2018, I wrote Blocking Windows Update on Windows 10 with C disk freespace, followed by Defending against Windows 10 bug fixes in October 2018 and Killing Windows Update on Windows 10 - a cheat sheet in December 2018. Eventually I concluded, in October of last year, The only way to fight Windows 10 spying is in your router - firewall rules won't cut it.
So, pretty ironic that, in this case, I was trying to restore Windows Updates.
To me, the issue is the loss of control, I want to be completely in charge of the installation of bug fixes. Thanks to Windows 10, we can no longer control which updates get installed (by and large) but, at least, I want to control when the updates are installed.
Microsoft also wants to be in charge and its their software, they have home field advantage. For example, this 2016 article by Daniel Petri (Windows 10 Ignoring the Hosts File for Specific Name Resolution) describes how the Hosts file is ignored for Windows Update. Thus, the best way to block Windows Update is from outside Windows.
| | ||
| Home => Windows Update vs. my Router | TOP | |
| michael--at--michaelhorowitz.com | Last Updated: May 29, 2020 11PM UTC | ||

Copyright 2001-2025 |
Copyright 2001-2025 |