| Michael Horowitz |
Home => Fighting Windows 10 Spying
|
| Michael Horowitz |
Home => Fighting Windows 10 Spying
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
October 15, 2019
One of the many ways I try to defend Windows 10 PCs from the spying Microsoft built into the Operating System, is with outbound firewall rules.
By default, any program running on Windows 10 can make an outbound connection to any computer on the Internet. Despite this, Microsoft wants to insure that dozens of components of Windows 10 can always phone home, so it includes outbound firewall rules that grant these components carte blanche. A tad greedy.
These firewall rules give me a target. I change around 30 or so rules from "Allow" to "Block" when setting up a new Windows 10 machine. One of the thirty, is the rule for the Windows Default Lock Screen. I don't know why the Windows Default Lock Screen needs to phone home and I don't care. I want to block it. And, I can. For a while.
A while?
Below you see two rules for the Windows Default Lock Screen. The top one allows it to phone home, the bottom one blocks it.
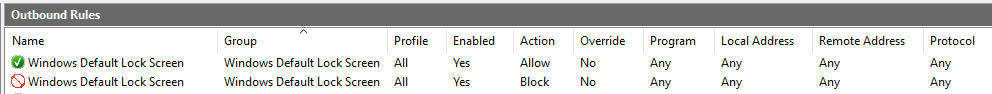
While there are no creation or update timestamps on firewall rules, trust me when I say that the Allow rule is fairly new and the Block rule was modified from an original Allow rule, by me, long ago.
After a period of time, Windows adds new firewall rules that allow many of the services that I had blocked. It does this for many components, even a few Xbox ones. Microsoft wants to insure that Windows 10 can phone home with god-knows-what data telling Microsoft all about our PCs. The same behavior exists with Windows Update. We can disable parts of Windows Update, but not all of it. The components that can not be disabled will eventually restore anything that we disabled.
We can't fight this fight on Microsoft's turf. It's their operating system and they have prohibited customers (victims?) from changing parts of it. The only way to prevent Windows 10 spying on us is by blocking the domains Microsoft phones home too. Perhaps this can be done in a router (via DNS or outbound firewall rules or parental controls), or with Pi-hole running on a Raspberry Pi or in a Docker container, or a free account from OpenDNS or with the Technitium DNS Server.
This is a big task, but the only one that has a light at the end of the tunnel. Anything else is telemetry whack-a-mole.
Update Oct 16, 2019: Then again, any device using Tor or a VPN will bypass network-wide controls. The same applies to encrypted DNS (DoH or DoT). I hope to soon look into two VPN providers that offer blacklisting of domains.
Update Oct 18, 2019: Dan Pollock maintains a list of bad domains to be used as a TCP/IP hosts file at someonewhocares.org/hosts/. One section of his list is devoted to Windows 10 reporting domains.
Update Oct 20, 2019: Another list of Microsoft domains is available from squidblacklist.org. They consider this a white list but it can be used in other ways too.
| | ||
| Home => Fighting Windows 10 Spying | TOP | |
| michael--at--michaelhorowitz.com | Last Updated: October 20, 2019 9PM UTC | ||

Copyright 2001-2025 |
Copyright 2001-2025 |