| Michael Horowitz |
Home => Insecure Banking Websites
|
| Michael Horowitz |
Home => Insecure Banking Websites
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
May 3, 2018
Recently while helping a couple people, I ran across the websites of two banks in the US. Each had security issues.
SOUTH CENTRAL BANK
The first bank was South Central bank in Kentucky. As you can see below, they brag about how secure their site is, now that they only use TLS version 1.2. The HTTPS that you see with a secure web page is, under the covers, implemented with either SSL or TLS. SSL is very old, TLS is newer. There are three versions of being TLS currently in use: 1.0, 1.1 and 1.2. Any company that truly cares about security will limit themselves to TLS version 1.2, as it is the most secure option. Very few sites do this however. Among the reasons for supporting older, vulnerable versions of TLS are backward compatibility. As shown below, old operating systems such as Windows XP and Vista will not work with TLS 1.2. Likewise, neither will Internet Explorer version 10. It is disgraceful how few websites limit themselves to TLS 1.2.

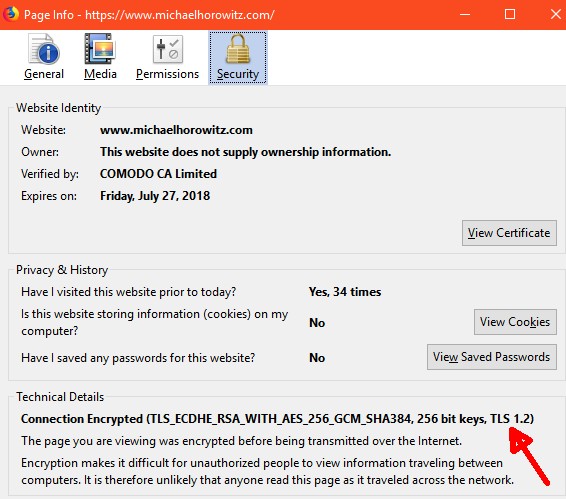
If you know where to look, Firefox version 59 on Windows displays the version of TLS used by the browser to connect with a website. First, click on the green lock, then, the caret/arrow pointing to the right, and then on More Information. This opens a window like that shown here. The red arrow indicates that for this website, this particular connection, used TLS version 1.2.
This website (michaelhorowitz.com) also supports TLS 1.1 and 1.0. I tried not to support these older protocols but the site runs on a shared hosting account and I don't get to make this choice. Doing so would require a more expensive type of account, or, my own server.
Sadly, every browser on every operating system does not display the version of TLS used to connect to the current web page. On Android, for example, Firefox does not while Chrome does.
You can tell which versions of TLS a website supports using the excellent Qualys SSL Server Test. Below is their report on the bank.
It turns out that www.southcentralbank.com does not support TLS 1.2 at all! It only supports TLS version 1.0. This is shameful, especially for a bank. On top of this, the Qualys report shows three other security problems.
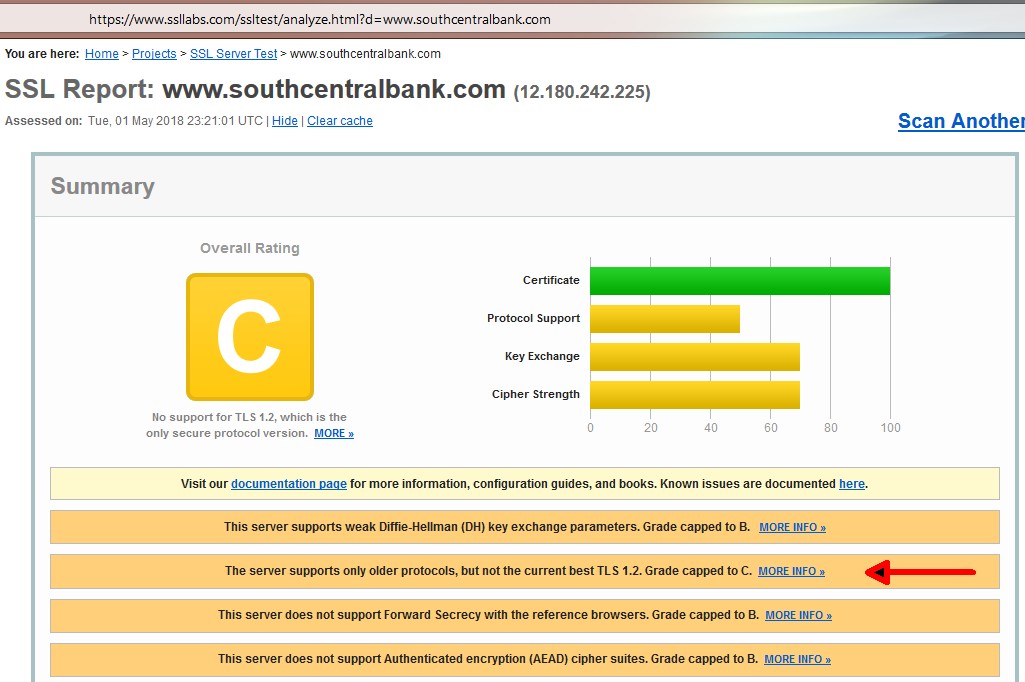
How can this be? When you open an online banking account with South Central bank, you don't do it at www.southcentralbank.com, you do it at SecureInternetBank.com. The South Central website fails to notify their customers that control over their online banking is being handled by someone else.
Who is SecureInternetBank.com? None of your business. A Whois search shows that the name is registered to "Domain Manager" which clearly shows that the people behind SecureInternetBank.com do not want to identify themselves. Need further proof? The website www.secureinternetbank.com does not even exist. South Central bank customers end up at web13.secureinternetbank.com. That site too, fails to load on its own.
That the South Central bank website is copyright as of 2015 (scroll to the bottom), is just another sign that there is no one home.
If I lived in Kentucky, I would use a different bank.
FIRST NATIONAL BANK
The second bank was First National Bank in Pennsylvania. Chrome on Windows would not display the online banking site at all, warning that "Your connection is not private." The site worked fine in Firefox. I ran the Qualys SSL Server Test on it to see what the problem was - and it turned out there were multiple problems, shown below.
As with the prior bank, this one also uses multiple domain names. The bank home page is fnb-online.com but online banking is done at banking.fnb-onlinebankingcenter.com. The report below is for the online banking domain/website.
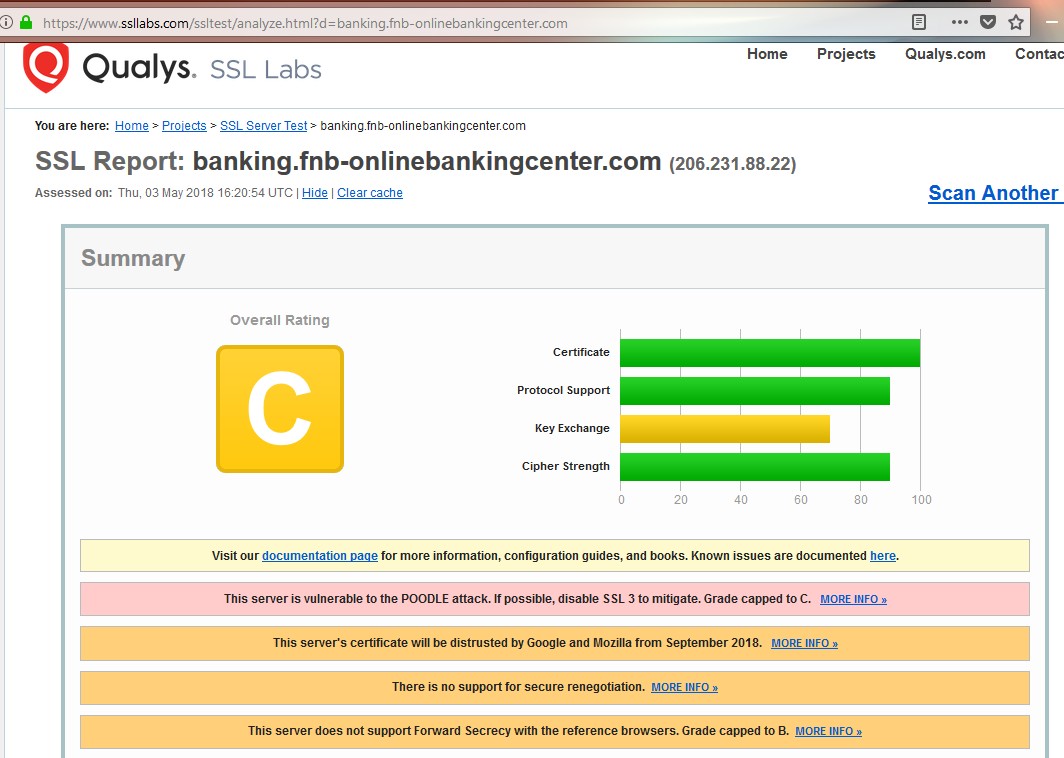
Beginning with the worst, the site supports SSL version 3 which is such a disgrace it's hard to put into words. Imagine renting a model T Ford on your next visit to Hertz. As for old buggy protocols, First National Bank scores a rare trifecta, in that it also supports TLS 1.0 and 1.1. To put this in context, see the first image above of South Central bank bragging that it only supported the secure TLS version 1.2. It may even be illegal for a bank to sill use SSL version 3. Not sure.
Of lesser import is the fact that the certificate needs to be replaced in a few months. It was issued by Symantec and they were found to be untrustworthy. I don't know enough about the lack of secure renegotiation to know how serious a problem it is.
I am, however, familiar with the last issue, the lack of Perfect Forward Secrecy (aka Forward Secrecy, PFS, FS). Suffice it to say that no website is secure if it does not support Perfect Forward Secrecy. Without it, all the rest is security theater, designed to fool the un-informed.
TAKE AWAY
The obvious conclusion here is that you should run the Qualys SSL Server Test on your banks' website. And, be aware, that you may have to do so on more than one domain.
There is no reason for any financial website not to score an A on the test. That said, the security of any website involves many different issues, it is not a simple yes/no, on/off, black/white thing. There may be some security issues even with a website that Qualys considers A-rated. But, that does not change the fact, that any and every financial website should score an A.
by Michael Horowitz
Minor updates May 4, 2018
| | ||
| Home => Insecure Banking Websites | TOP | |
| michael--at--michaelhorowitz.com | Last Updated: May 4, 2018 3 PM | ||

Copyright 2001-2025 |
Copyright 2001-2025 |