| Michael Horowitz |
Home => Hiding on a Wi-Fi network
|
| Michael Horowitz |
Home => Hiding on a Wi-Fi network
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
August 4, 2021
Recently, I stayed at a Bed and Breakfast that used Eero to provide Wi-Fi around the inn. Guests were instructed to use the private, password protected network, which, at first, I did. But, when I scanned for nearby networks, I saw that the Eero system was also creating a Guest Wi-Fi network, one without a password.
The knee-jerk reaction is, of course, to avoid the open Wi-Fi network. But, I preferred it because it offered better hiding.
The knee-jerk reaction to open Wi-Fi networks is based on the lack of over-the-air encryption. Sure secure (HTTPS) websites are now in the majority, but still, a computer/phone/tablet can (and does) send all sorts of un-encrypted data. Without over-the-air encryption, this unencrypted data can be read by anyone with the necessary skill, and you don't need much skill.
The main point of this blog is that the encryption of data sent over the air is not the be-all and end-all of Wi-Fi security. Hiding on the network is just as important. Hiding means that your computer/phone/tablet is not visible to the other devices/people on the same network. Not even a highly skilled bad guy can hack into a device they can not see.
The first thing a bad guy will do is scan the network to see what other devices are also using it. There are many LAN scanner applications. For Android, I recommend the Network Analyzer Pro app by Jiri Techet. It costs $4 in the US and there is also a free version. The screen shots below were created with Network Analyzer Pro. I also use Fing which is available on multiple operating systems.
Below is a LAN scan of the private Wi-Fi network at the inn.
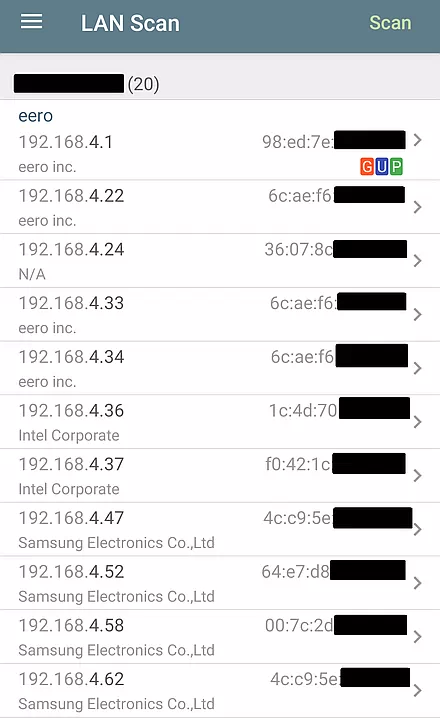
There were 20 detected devices with the main router being at 192.168.4.1. A private network is intended for trusted devices, so all devices on the network, by default, can see each other. This is by design.
But, it makes me nervous.
If my phone/computer/tablet can see these other Wi-Fi devices, then they can see me too. Someone with sufficient technical competence might use this visibility to abuse any open TCP/IP ports on my phone. Or, they might look for exploitable bugs in the software on my phone. It is safer to use a Wi-Fi network where other devices on the same network can not see our device(s).
With Eero at least, the Guest network works that way. Devices on an Eero Guest network can see the Internet, but not each other. I tested this by doing the same LAN scan with two of my devices connected to the Eero Guest network. The scan only saw the device it was running on and the router. I was safely isolated from other guests that may or may not have been using the Guest network.
This makes sense. Most of the time we only need to give Guest users Internet access, they do no not need to interact with each other.
This is not to say that all routers do the same thing on their Guest networks. A few have a configuration option for this, most say nothing about it at all. My favorite router company, Peplink, does have an option for this, they call it Layer 2 Isolation. When it is enabled, devices on the wireless network can not see each other.
Speaking of VPNs, you can (and should) use a VPN, even on password protected Wi-Fi networks. There is nothing wrong with double encryption.
AND...
The LAN scan above shows the MAC address of detected devices on the network. There are two parts to a MAC address. The leftmost part identifies the company that made the network adapter, in this case, the Wi-Fi radio. This is how the scanning program knows that a given device was made by Samsung or Eero. The rightmost part identifies one specific piece of hardware. Think of it as a unique serial number for each Wi-Fi radio. This is why I have redacted that part of the MAC address in the screen shot above.
The arrows pointing to the right offer additional tests that Network Analyzer Pro can perform on specific devices. The most invasive is a port scan looking for open ports. It can also Ping and Traceroute a specific device. In the LAN scan below you will see one device with a blue W which indicates that that device offers a web interface. Let the hacking begin.
A week later, I visited a large medical facility and the Wi-Fi experience was exactly the opposite. On that Guest network, everyone could see everyone else, and there were over 300 devices on it! Part of the LAN scan is shown below.
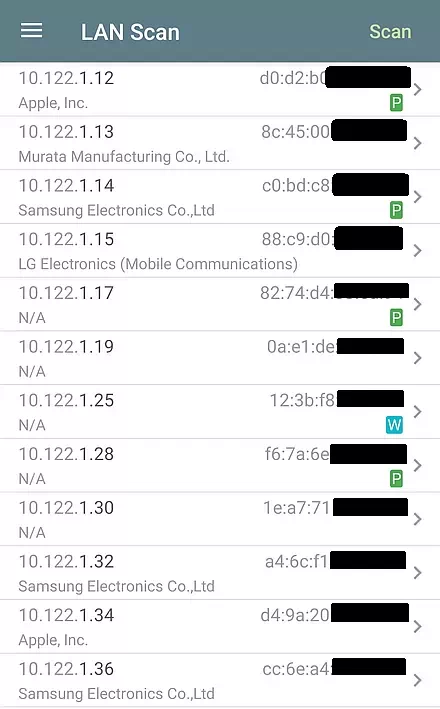
Typical of a large organization they were using high-end expensive hardware. The router was made by Palo Alto Networks and the many Access Points were made by Cisco. Not only could Guest Wi-Fi devices see each other, the web interface for the Access Points was open to Guest users. Yikes.
Defensive Computing on this Guest network is no small feat. While a VPN or Tor encrypts data sent to/from the Internet, hiding your presence from the other devices on the same network is a whole different thing.
In the old days, the advice for Windows used to be to disable File and Printer sharing on public networks. Now, Windows lets you chose whether to treat a network as public or work or home. What exactly does that mean? Microsoft does not say.
If the operating system offers a firewall, then it needs to be configured so that all TCP and UDP ports are stealthed. That's over 130,000 ports. This is so that any and all unsolicited data sent to the device is ignored. In the other direction, the TCP/IP routing table needs to be configured so that the system is blocked from sending any data to the subnet where it resides. In this example, that means blocking outbound data packets targeted at 10.122.1.x.
Hiding devices from each other is really the job of a router. VPN software is not involved with the LAN side of things. VPNs deal with data coming and going from the Internet.
I have tried my fair share of VPN software from assorted VPN providers. Only two offered this feature and it only worked on one: the Mullvad Windows VPN client. Mullvad offers software for other operating systems, but at the time I tested, only their Windows software offered to block LAN-side access. The option is called Local Network Sharing.
To me, this should be a prime consideration when choosing a VPN. But, it is never mentioned in any VPN review.
The next time you use a public Wi-Fi network, you might want to run a LAN scanning app. In the best case, all you will see are the router and your device.
Years ago, I went to a concert, ran a LAN scan and saw many other devices. The venue was using Aruba hardware and I later verified that Aruba can isolate Wi-Fi users. When I tried to contact the venue, I got nowhere. Beats me why simple security steps don't get taken.
| | ||
| Home => Hiding on a Wi-Fi network | TOP | |
| michael--at--michaelhorowitz.com | Last Updated: October 3, 2021 4PM UTC | ||

Copyright 2001-2025 |
Copyright 2001-2025 |