| Michael Horowitz |
Home => Routers are under constantly being probed
|
| Michael Horowitz |
Home => Routers are under constantly being probed
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
March 19, 2018
Recently, I was looking at the router of a Verizon FIOS customer. The router was an old ActionTec MI424WR-GEN2 (Firmware Version: 20.21.6) with a feature that I find fascinating, a firewall log (the router calls it a security log). Not all routers have logs and some that do, such as Asus, log internal events that only Linux networking experts can understand. But this router had a log network events.
As someone who has been writing about Defensive Computing since 2007, the most interesting network event, to me, is an unsolicited incoming connection attempt. If I were into clickbait, I would call this an attack. The reason routers have firewalls, is to prevent unknown computers on the Internet from making unsolicited connections into the computers behind the router - our assorted computing devices.
BACKGROUND
Whenever two computers communicate over the Internet, their conversation is uniquely identified with an IP address and a port number.
Every computer on the Internet has a unique number that techies call an IP address. At least they did in the beginning. Now, routers are assigned a public IP address (a 32 bit number) and our computers/phones/tablets have private IP addresses that are only valid in our home. To the outside world, all of our computing devices have the same public IP address, the one that is assigned to the router.
Ports, in this context, are a networking thing. More exactly, a TCP/IP thing. Ports are what let a single computing device have multiple concurrent conversations with other computers. Each conversation is assigned a unique port number. Port numbers go from 1 to 65,535.
My personal website, michaelhorowitz.com, is available using two different port numbers, one for insecure HTTP and another for secure HTTPS. For secure access, typing
https :// michaelhorowitz.com
is the same as typing
https: // michaelhorowitz.com:443
Port 443 is the default port used for secure web pages.
On the insecure side, typing
http :// michaelhorowitz.com
is the same as typing
http :// michaelhorowitz.com:80
Port 80 is the default port for insecure web pages. Up until July 2017, this would display the site using HTTP. Since then, I automatically re-direct all HTTP requests to HTTPS. Still, the initial connection was to port 80.
All other port numbers will fail. For example, feel free to try port 441 (http://michaelhorowitz.com:441) or port 442 (http://michaelhorowitz.com:442). A computer functioning as a web server, does not listen for web page requests (or for anything) on these ports. In techie lingo, ports 441 and 442 are closed (or stealthed). A Shodan report on the computer running this very website shows that it has 3 open ports, which implies that the other 65,532 are closed.
With this as background, we can now understand the firewall log in the Verizon router.
FIREWALL LOG
Below is a condensed and edited version of the firewall/security log from the Verizon FIOS router. The log covers nine minutes; 3:47pm to 3:56pm on March 13, 2018. The time was selected by happenstance. The log had filled up earlier, I reset it on the 13th and waited for it to fill up again. There were other records on the log too, what's shown below are just the unsolicited incoming connection attempts (attacks) that the firewall blocked.
Each line starts with the time in HH:MM:SS format and the message that an inbound connection was blocked. "Traffic" is nerd lingo for a bunch of bits and bytes traveling over a network. The next field is the source IP address, a colon, and the source port number. "Source" is nerd lingo for the computer that tried to make an unsolicited connection into the router. The source port number is of no interest. After the arrow, is the public IP address of the router, which I have replaced x.x.x.x. The final field is the port number that the outside computer tried to contact. All connection attempts were via TCP.
|
15:56:07 Inbound Traffic Blocked - 172.217.3.99:443 -->x.x.x.x:39227 15:55:35 Inbound Traffic Blocked - 60.10.56.170:50597 -->x.x.x.x:1433 15:55:31 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:2078 15:55:09 Inbound Traffic Blocked - 77.72.82.125:47395 -->x.x.x.x:6386 15:55:08 Inbound Traffic Blocked - 77.72.82.22:58351 -->x.x.x.x:6613 15:55:05 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:3966 15:54:59 Inbound Traffic Blocked - 80.82.65.231:51166 -->x.x.x.x:7972 15:54:57 Inbound Traffic Blocked - 60.17.227.119:20990 -->x.x.x.x:23 15:54:21 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:2130 15:54:10 Inbound Traffic Blocked - 162.243.149.64:50492-->x.x.x.x:20 15:53:41 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:1479 15:53:34 Inbound Traffic Blocked - 189.79.247.253:14450-->x.x.x.x:23 15:53:33 Inbound Traffic Blocked - 185.143.223.202:53184->x.x.x.x:22 15:53:30 Inbound Traffic Blocked - 77.72.82.57:55794 -->x.x.x.x:6767 15:53:13 Inbound Traffic Blocked - 77.72.85.8:43887 -->x.x.x.x:58913 15:52:40 Inbound Traffic Blocked - 77.72.82.80:45939 -->x.x.x.x:8329 15:52:36 Inbound Traffic Blocked - 180.20.165.43:17913 -->x.x.x.x:23 15:51:56 Inbound Traffic Blocked - 59.16.116.114:27092 -->x.x.x.x:2323 15:51:47 Inbound Traffic Blocked - 39.135.17.43:161 -->x.x.x.x:33949 15:51:28 Inbound Traffic Blocked - 185.56.81.55:14957 -->x.x.x.x:5900 15:51:09 Inbound Traffic Blocked - 191.101.167.83:50889-->x.x.x.x:33899 15:51:05 Inbound Traffic Blocked - 108.30.240.156:33475-->x.x.x.x:23 15:50:59 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:2052 15:50:37 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:3731 15:49:59 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:1780 15:49:50 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:1797 15:49:26 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:1626 15:49:19 Inbound Traffic Blocked - 23.24.96.174:47514 -->x.x.x.x:3434 15:49:12 Inbound Traffic Blocked - 5.188.11.89:50007 -->x.x.x.x:13300 15:49:11 Inbound Traffic Blocked - 181.214.87.50:59134 -->x.x.x.x:4389 15:49:00 Inbound Traffic Blocked - 185.106.128.214:80 -->x.x.x.x:46687 15:48:56 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:275 15:48:44 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:552 15:48:39 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:617 15:48:37 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:854 15:48:26 Inbound Traffic Blocked - 191.101.167.7:56994 -->x.x.x.x:1228 15:47:26 Inbound Traffic Blocked - 77.72.82.22:58351 -->x.x.x.x:6197 15:47:01 Inbound Traffic Blocked - 121.55.151.94:28000 -->x.x.x.x:23 |
| Verizon router firewall log |
There were 38 connection attempts in these 9 minutes, just over 4 per minute. There is no reason to think these nine minutes are any different from any other nine minutes. Multiplied out, this would be 6,080 connection attempts per day. You can see my interest in Router Security.
WHO ARE THESE GUYS
Its hard for me to identify the bad guys trying to get into this router. The website www.iplocation.net checks multiple databases with IP address location information. In most cases, different databases returned different results.
That said, among the IP addresses with the most agreement as to their owner and location is the first one, 172.217.3.99 which belongs to Google. The second computer, at IP address 60.10.56.170 is very likely in China. IP address 162.243.149.64 seems to belong to Digital Ocean in California, while 59.16.116.114 seems to be in South Korea and 23.24.96.174 probably belongs to a Comcast Cable customer in either Maryland or Virginia.
Still, this does not tell us much. If the bad guy IP address was a VPN server, then it is likely that the VPN provider would not know which of their customers was probing this router. And, if the source IP address was a coffee shop, there is no way the owners could pin down the bad customer. Likewise, if the source was the router for a business, they probably could not pin down the bad employee. If Digital Ocean does run one the of the attacking IP addresses, they may or may not be able to link it to a specific customer - it depends on whether the Virtual Private Server gets a dedicated IP address or not. However, if the source was a home Comcast customer, then Comcast certainly could identify the customer.
The computing neighborhood around 77.72.82.x seems particularly suspicious. There were connection attempts from 77.72.82.125, 77.72.82.57, 77.72.82.80 and twice from 77.72.82.22.
TARGETED PORTS
IP address 191.101.167.7 made the most queries, 14. They were to ports 1797, 1479, 2130, 2052, 1780, 1626, 3966, 275, 552, 617, 854, 1228, 2078 and 3731. My guess is that the computer is trying to find all the open ports and trying them in a random sequence to avoid detection.
The computer at IP address 191.101.167.83 tried to get at port 33899 which is used by Microsoft Remote Desktop, software that lets you log in to a remote Windows computer. From the perspective of the bad guys, the home of this Verizon customer is remote.
There were five attempts in these nine minutes to connect to port 23 which is used by Telnet.
Port 5900 came under attack, it is used by VNC which, like Microsoft Remote Desktop, lets people log in to a remote computer. VNC supports many operating systems, it is not limited to Windows.
There were also connection attempts to port 22 (used by SSH), port 20 (used by FTP) and port 1433 which is used by the Microsoft SQL Server database.
The infamous Mirai botnet, and its derivatives, scan for ports 23 and 2323, looking for vulnerable IoT devices. The computer at IP address 59.16.116.114 tried to connect to port 2323.
OPEN PORTS?
The log above indicates connections that the router blocked. What about connections it did not block? Were any computers on the Internet able to make an unsolicited connection to the router, or, to a computer behind the router? Don't know. Can't tell. Verizon does not log that.
The larger question though is what ports are open, and thus vulnerable to attack?
The most secure answer is that no ports are open (this is a bit of a simplification as ports can be either Closed or Stealthed). This would block every computer on the Internet from connecting in to either your router or your computing devices. My favorite router, the Pepwave Surf SOHO blocks all ports by default. I recently tested a mid-range TP-Link router and it too, blocked all 65,535 ports.
As for this router, Verizon configured it with at least five open ports as you can see below in the display of Port Forwarding done by the router.
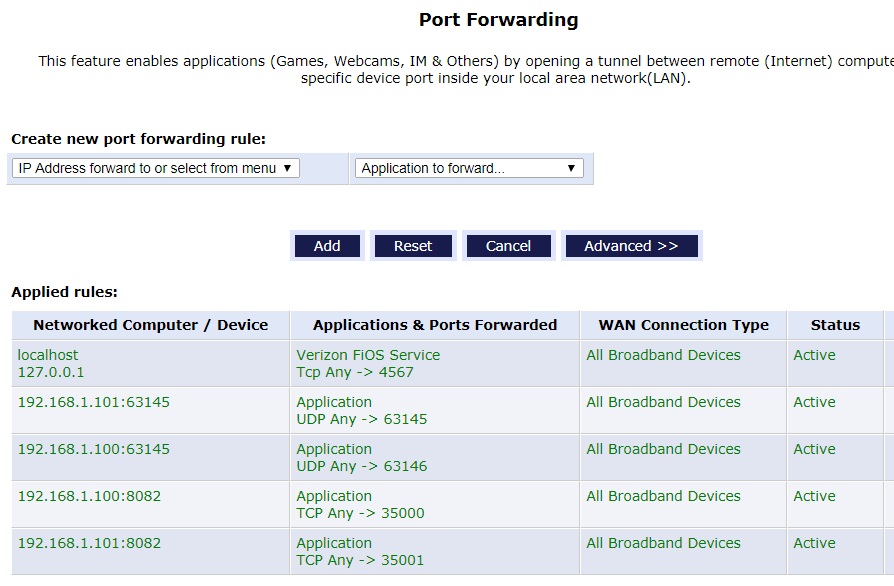
The first line directs incoming TCP connections to port 4567 to the router itself. The name localhost and the IP address 127.0.0.1 always refer to the computing device they are running on. Port 4567 is a known back door that Verizon sets up in their routers for their own use. This router is thus subject to manipulation by many Verizon employees.
The next four forwarding rules send data to the two TV set top boxes in the home. They are at IP address 192.168.1.100 and 192.168.1.101. Incoming connections using TCP targeted at port 35,000 go to the box in the Living Room, those directed at port 35,001 go to the box in the Bedroom. Incoming connections using UDP targeted at port 63,145 go to the box in the bedroom, UDP requests to port 63,146 go the box in the Living Room. Hackers fluent in set top box protocols could probably manipulate and re-configure the boxes.
Each set top box, and the router itself, are vulnerable to attack because Verizon left a door open. They poked five holes in the firewall.
It is not uncommon for an ISP, such as Verizon, to give their customers routers with open ports. This is partly why I recommend not using a router from your ISP, if at all possible.
Does this router have an other open ports? It's hard to know. Programs running on the router can also open ports. Routers that support UPnP and/or NAT-PMP can be instructed to open ports by any attached computing device.
There are many websites that will test the ports on your router and report whether they are open or not. I have a list on the Test Your Router page of my RouterSecurity.org site. But, they are all incomplete.
A complete report requires testing all 65,535 TCP ports, and all 65,535 UDP ports. Only nerds fluent with port scanning software, really know if their routers have any open ports. The rest of you are on your own.
For more on router security, see my RouterSecurity.org website. Remember, 6,000 attacks per day.
| | ||
| Home => Routers are under constantly being probed | TOP | |
| michael--at--michaelhorowitz.com | Last Updated: March 19, 2018 6 PM | ||

Copyright 2001-2025 |
Copyright 2001-2025 |