| Michael Horowitz |
Home => Using ProtonMail encrypted messages with normal email
|
| Michael Horowitz |
Home => Using ProtonMail encrypted messages with normal email
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
October 2, 2021
The superpower that ProtonMail brings to the table is easy, simple, no-brainer encrypted email messages between ProtonMail users. The encryption just happens, you don't need to do anything. Everyone should have a ProtonMail account.
But, since not everyone does, this is a cheat sheet on sending an encrypted message from ProtonMail to someone using normal standard email such as Gmail, Yahoo, Outlook, Hotmail, AOL, etc.
The conversion between secure ProtonMail and insecure normal email is handled by a web page.
Rather than sending the actual message, ProtonMail sends the recipient a normal email message (sample below) saying they need to view a web page. The actual message is on the web page. The kicker is that to view the web page with the message, the recipient needs to know a password.
How the recipient gets the password is up to the sender and recipient. There is no one right answer. A phone call, smoke signals, secure messaging software (such as Signal or Threema), an index card in their lunch box, whatever works for the sender and recipient. Two wrong answers are normal email and text messages as neither is the least bit secure.
In the screen shot below, someone at the ProtonMail.com website is creating a new email message. The option to encrypt the message, for those not in the ProtonMail club, is the lock icon at the bottom, indicated by the red arrow.
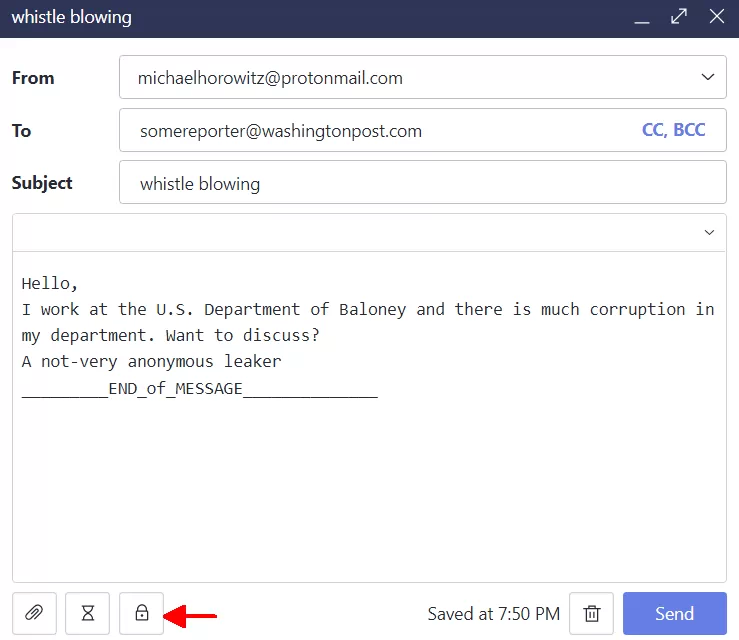
Click the lock and you are prompted for the password (shown below) and, optionally, a hint.
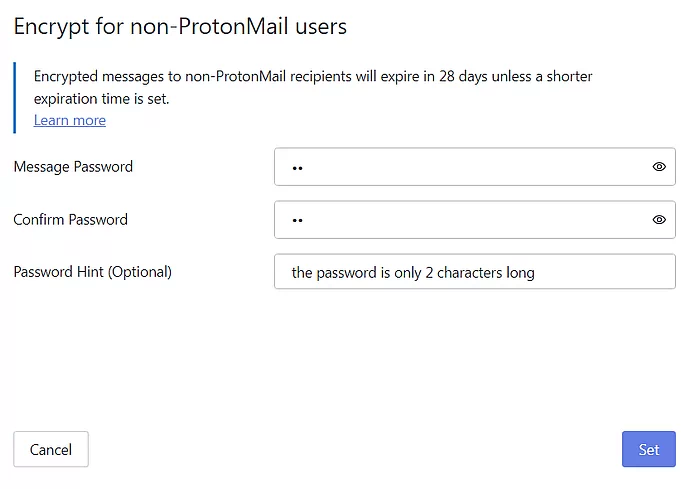
There do not seem to be any rules for the password, but as always, longer is better. Sad to say, in my test it accepted a two character password. Ugh.
After entering the password, the lock icon changes from lite gray to blue. Also, a blue lock now appears just to the left of the recipient email address.
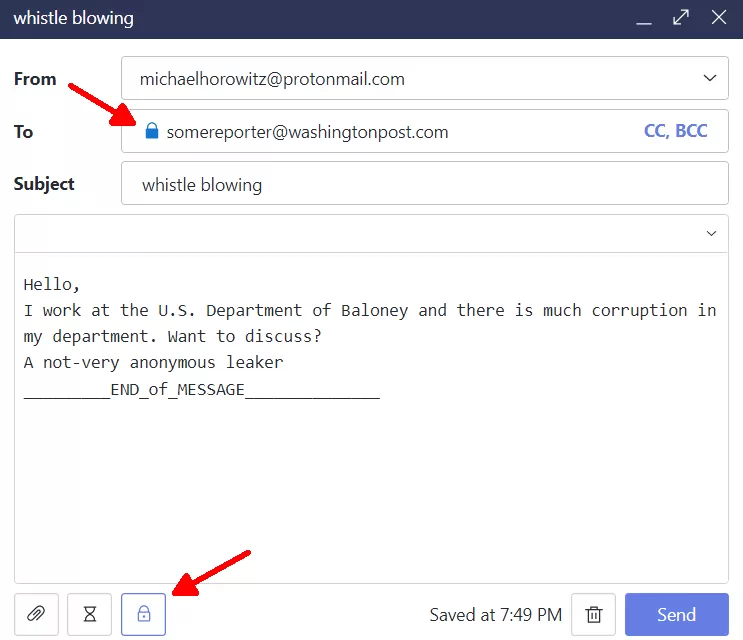
The hourglass icon in the bottom left corner is where you can set an expiration time for the message.
Needless to say, click the blue SEND button at this point.
Below is what the recipient will see in their inbox. Note that the hint is front and center.
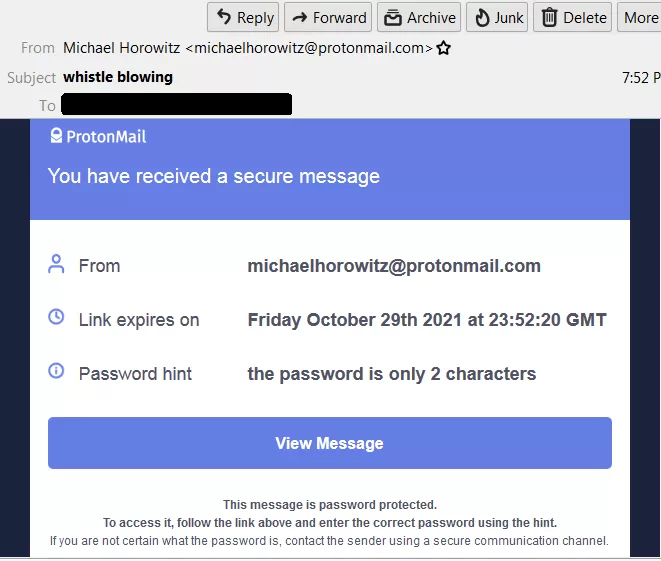
The link behind the blue View Message button looks like this
https://mail.protonmail.com/eo/UpnBHuNp0N1Xm9acpWjN_yooDUY5XZAo4102mPpzEtYXI_Iim19K48TzjoXrIE9vd3gnoN4aNq
As you see below, we get re-directed from mail.protonmail.com to old.protonmail.com.
Instead of being asked to enter the password, the recipient is prompted to decrypt the message.
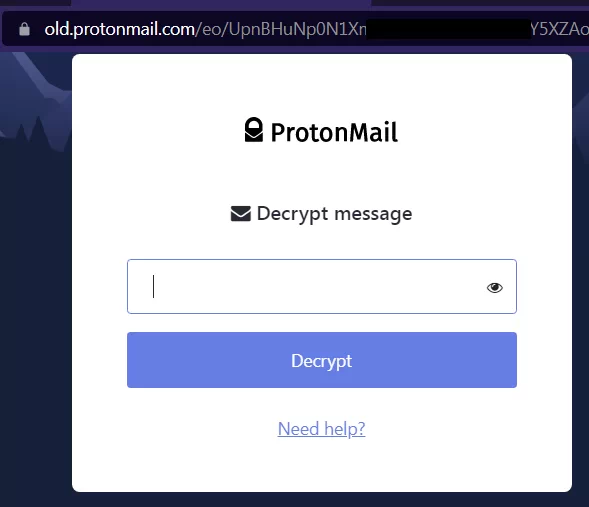
While you might think the system has some brute force protection, it does not seem to. I entered the wrong password 20 times without being permanently banned.
Below is the end of the road, the screen shot shows the recipient viewing the secure web page/email message.
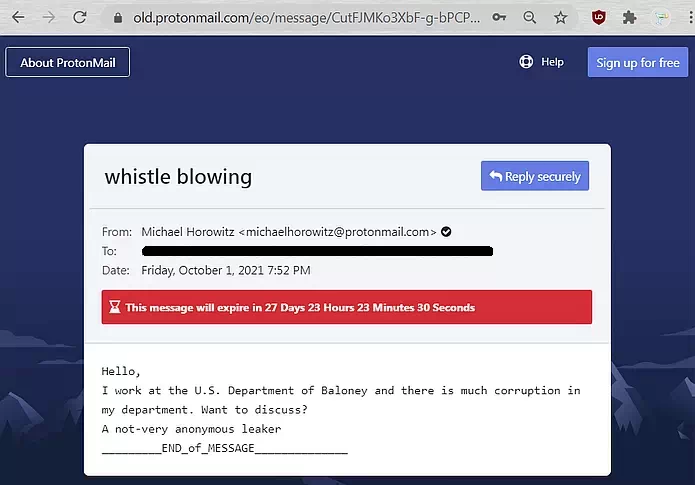
Is this really secure? Not necessarily. It is only as secure as your web browser. More specifically, it is only as secure as the extensions installed in your web browser. The security of browser extensions is an industry disgrace. Far too many extensions can see and manipulate every web page. This is a familiar soap box for me, I have stood on it before. The recipient is much more secure if they view the message in a browser with no extensions. Yet, no one says this.
Another insecure aspect of this has to do with metadata. There is no hiding the fact that the sender and recipient communicated. Sometimes, just that knowledge can be dangerous. Likewise, the subject line of the email is exposed to being spied upon.
Computer techies get hung up on the encryption while ignoring anonymity. This is why I chose the sample email message that I did. Clearly, it is important for the whistle blower sending the message to be anonymous. Yet, a million recommendations to use Signal for secure communications, ignore the fact that a Signal userid is a telephone number. ProtonMail is outstanding here in that anyone can create a free ProtonMail account without providing personal information. THIS IS HUGE in the real world, but not the world most of the tech press inhabits.
And, let's not forget both the two character password and the lack of protection from brute force password guessing. I wonder if Tutanota does this better?
I was also disappointed to see that old.protonmail.com is protected with a certificate from Lets Encrypt. The upside of Lets Encrypt is that it is free. The down side is that it does not authenticate websites. In techie terms, Lets Encrypt does not offer Extended Validation. That is, they don't verify that old.protonmail.com really truly belongs to ProtonMail. Of course it does, but Extended Validation insures that the web page you are viewing is from the real old.protonmail.com site rather than a scam copy of it. It is not just the "old" subdomain, the main ProtonMail website also uses LetsEncrypt. Sad to see.
In fairness, very few websites bother to pay for Extended Validation any more.
| | ||
| Home => Using ProtonMail encrypted messages with normal email | TOP | |
| michael--at--michaelhorowitz.com | Last Updated: October 23, 2021 10PM UTC | ||

Copyright 2001-2025 |
Copyright 2001-2025 |