| Michael Horowitz |
Home => HoverOverLinks
|
| Michael Horowitz |
Home => HoverOverLinks
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
February 16, 2020: Initial creation
February 20, 2020: Added Google example
March 28, 2020: Added a real world example
April 27, 2020: Added a new section on server side re-directs
May 14, 2020: Expanded the section on Server-Side Re-directs
Sept 30, 2021: Added link to a blog article about the Google Search Engine and link manipulation
Feb 5, 2022: Added link to an article about Linkedin re-directs being abused
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Enough already. Far too many Art History majors working in the tech press keep recommending that you hover the mouse over a link to see where the link will actually lead. This is a scam. The link displayed in the bottom of the web browser window, when you hover over the link, can not be trusted. Here is proof.
This appears to be a link to a good website. When the mouse hovers over this link, it will appear that it goes to www.somegoodplace.com. Click it. I dare you :-)
The link really goes to guce.advertising.com. JavaScript is used to dynamically change the link just as it is clicked. Pretty cool, eh?
The JavaScript code that makes this possible is quite simple. To begin with, here is what a normal link looks like in HTML:
< a href="https://www.somegoodplace.com">link to good site< /a>.
Below is that same link with the added JavaScript code that makes the malicious swapping possible. The magic is in the "onclick" event.
< a onclick="this.href='https://guce.advertising.com';"
href="https://www.somegoodplace.com">link to good site< /a>.
Of course, there is no mouse with a smartphone or tablet, but the issue is there too. To see where a link goes, simply long press on the link. Here is a screen shot of what this looks like in the Chrome browser on Android 10. Interestingly, if, from this menu, you chose to open the link, the browser goes to the good destination. Likewise, copying or sharing the link copies/shares the good destination, so these are great defensive tactics. Just don't click the link.
The situation is similar with Safari on iOS. As this screen shot shows, it too, displays the good link when long pressed, and if you opt from the menu to open the link, it will open the good link, not the bad one. Here too, however, clicking the link goes to the bad website.
There is nothing new here, Google has been lying about the destination of links for longer than I can remember. Take this search for "George Washington University" for example.
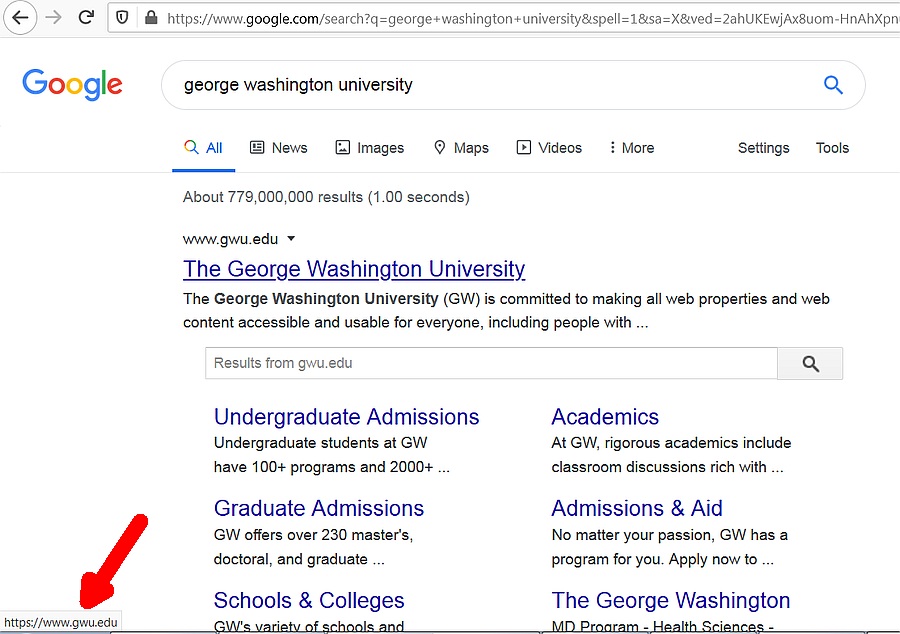
The mouse pointer does not appear in the screen shot but it was hovering over George Washington University, and the bottom left corner of the window indicates that the link goes to www.gwu.edu. That's not true. This is the actual link:
https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&cad=rja&uact=8&
ved=2ahUKDwj5h4Kqm-HnAhUSVd8KHRABD8YQFjAAegQIGBAD&
url=https%3A%2F%2Fwww.gwu.edu%2F&usg=AOvVaw3cfAPnGFZ4GkR8LQNcuLdm
which I got by simply right clicking on the link and copying the Link Location. I added some line breaks to make it easier to read. When you click on a link in Google search results, you first go back to Google, then to the destination that the link appears to point.
Update Sept 30, 2021: This article, Don't track me Google for Firefox blocks links manipulations by Google when clicking or copying by Martin Brinkmann, points out that this link manipulation is not used in the Chrome browser.
In addition to the technology, there is also a lesson here on trust. If you ever see this advice in the future, you know not to trust the person who offered it. Even moreso, what does it say when a large organization repeats this old fallacy? It shows that no one in the organization reviews what they publish. I'm looking at you Consumer Reports and WireCutter.
On a related note, shortened links are also dangerous, they are just more obvious about it. Defensive suggestions for dealing with shortened links can be found in the Extra Credit section of my DefensiveComputingChecklist.com website. Don't trust this link? I don't blame you :-)
SERVER SIDE RE-DIRECTS
April 27, 2020. Then too, there are server side re-directs that require no Javascript at all. For example, the very trustworthy Ask Woody website sends out newsletters with links like this:
https://askwoody.us19.list-manage.com/track/click?u=549ef5d038a469ebdf97ac1&id=d62a29ac7&e=82b076b0e
Clicking on this link can send you anywhere Woody wants you to go. There are three parameters in the above link, "u", "id" and "e". My guess is that one is a code for the web page that you end up at, another identifies you in the AskWoody.com newsletter system and the third is an account at list-manage.com.
There is nothing malicious here, at least not in the case of Woody Leonhard, but the point is that what you see as the initial link tells you nothing about the web page where you eventually end up.- - - - -
May 14, 2020. The WireCutter website offers many examples of server side re-directs. For example, some links at the site look like this:
https://thewirecutter.com/out/link/99999/999999/9/99999?merchant=Amazon
Where the 9s represent a number. When clicked, you are obviously taken, first, to the WireCutter website, but just for a second before they re-direct you to the retailer, in this case, Amazon.com.
Some other links on the site look like this:
https://shop-links.co/99999999999999999999
In my experience, after going to shop-links.co, this link goes to
https://api.bam-x.com/api/v0/click_auction/?a=999999999999999999
and only then, finally, takes you to to retailer selling the product in question. In this case you are bounced twice before landing at the ultimate destination. I found two other instances of server-side re-directs where you were bounced twice before landing on the retail product page.
In one case, the links looked like this
http://www.anrdoezrs.net/links/9999999/type/dlg/sid/EDTESTzz99999/https://electronics.woot.com/xxxxxxxxxxxxxxx
which, after starting at androezrs.net, then goes to emjcd.com before finally going to the retailer (in this case woot.com).
They also have links that look like this
https://go.skimresources.com/?id=999999999999&xs=1&url=xxxxxxxxxx
which make a stop at bizrate.com after skimresources.com and before finally landing at the retailer.
- - - - - - - - - - - - -
UPDATE: February 5, 2022. LinkedIn has a re-direct service that bad guys have been abusing for years. The link looks like this
https://www.linkedin.com/slink?code=99999
It starts at linkedin.com but does not stay there. See How Phishers Are Slinking Their Links Into LinkedIn by Brian Krebs. February 3, 2022
- - - - - - - - - - - - -
UPDATE: March 27, 2020. This article, New Router DNS Hijacking Attacks Abuse Bitbucket to Host Infostealer by Liviu Arsene of BitDefender describes how a malicious web page tricks Windows users into installing malware. Part of trickery is disguising the destination of a link. Quoting: "The download button has the 'href' tag (hyperlink) set to https://google.com/chrome so it seems clean when the victim hovers over the button. But actually an 'on-click' event is set that changes the URL to the malicious one..."
- - - - - - - - - - - - -
NOTE: The first version of this blog used a different approach. Instead of the "onclick" event, it used the "onmouseover". This approach fools the desktop version of Firefox, but does not fool Chrome or Edge. On iOS, the onmouseover approach fools both Safari and Firefox. However, on Android, it does not fool Chrome, Firefox or Brave. On Android, it only fools the DuckDuckGo browser. The "onclick" event seems to fool every browser.
| | ||
| Home => HoverOverLinks | TOP | |
| michael--at--michaelhorowitz.com | Last Updated: February 5, 2022 5PM UTC | ||

Copyright 2001-2025 |
Copyright 2001-2025 |