| Michael Horowitz |
Home => A hidden Firefox feature easily verifies websites
|
| Michael Horowitz |
Home => A hidden Firefox feature easily verifies websites
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
July 15, 2018
That a website is "secure" is only half the story. When web browser software (and nerds too for that matter), refer to "secure" websites, it means that the website uses encryption to scramble data it sends (web pages) and receives. But many scam/fake/malicious websites are considered "secure".
What too many people fail to consider, is who owns/runs/manages the website in question. This website, for example, could well be run by a guy named Jim Jones. Nothing about this site insures that someone named Michael Horowitz is really behind it. What this, and most "supposedly secure" websites lack, is a partial third party vouching for the entity that owns and run site site.
Identity assurance exists, but it costs money; more than I am willing to spend for this site. Website assurance is issued by any of hundreds, if not thousands, of companies called Certificate Authorities. A certificate is a file that carries within it, the identity verification. Our web browsers, trust the Certificate Authorities, and they, in turn, vouch for websites willing to pay for the service.
Needles to say, any company that cares about the security of their website will pay the extra fee to have their identity verified. You can see how Firefox 61 on Windows displays the two types of "secure" websites below. Both use HTTPS. Both are flagged with a green padlock icon.

Firefox 61 displaying two types of secure websites, with and without identity verification
For this website, that's all there is to say about it. However, the CIA has had its website verified and this is indicated by the green "Central Intelligence Agency (US)" between the green padlock and the HTTPS.
Why bother with identity verification? If a web browser says you are at cia.gov, then you surely are at the website of the CIA. No? No.
Manipulation of DNS and probably other networking tricks can land you at a scam website that appears as cia.gov in a web browser. Not only that, even if you are connected to the real CIA website, you could still be the victim of a Man-in-The-Middle attack. The entity sitting between you and the CIA (in the middle) can log data traveling in each direction and, if they so desire, manipulate it too. Many articles say that "secure" websites are protected from Man-in-The-Middle attacks. This is not true.
On top of this, all verification is not the same. The CIA got its verification from a company called DigiCert (or, at least I think they did, no one ever bothers to tell the public who their Certificate Authority is). Anyone who encounters a copy of cia.gov that was verified by a different Certificate Authority is looking at a scam site. Needless to say, a supposedly "secure" instance of cia.gov that does not have any identity verification is also a scam, as would be an insecure (HTTP) copy of cia.gov.
The company that did the identity verification for a website is crucial in detecting a Man-in-The-Middle attack. In the case of the CIA website, for example, the entity in the middle will forge a copy of the cia.gov website that may well be a perfect duplicate (if they are only logging data, not manipulating it) except that the forged copy would not have gotten its certificate/validation from DigiCert. Typically a Man-in-The-Middle attack will present the victim a scam copy of the targeted website that does not have any identity protection, or does not use encryption at all. Typically. It is, however, possible for the scam website to also scam the identity verification. But doing so, requires a using a different Certificate Authority, one that has been compromised in some way.
Note that if you are an employee of a large company, Man-in-The-Middling may be the norm rather than the exception. Some employers want to evaluate all data entering and/or leaving their network and they do so by placing Man-in-The-Middle boxes at the edge of their network. The boxes dynamically create certificate files that are trusted by employee computers because a special Certificate Authority has been installed on the computers of the employees.
All this leads me to a very important point - finding out who vouches for a website is harder than it should be. The information is available, but its typically buried in the browser interface.
|
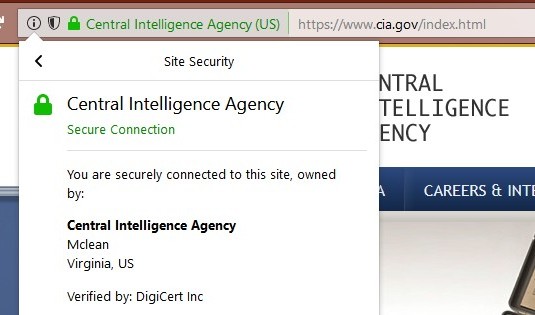
For example, Firefox 61 on Windows requires 2 clicks before you can see that DigiCert is vouching for the CIA. First, you have to click the I in a circle, then on the half arrow pointing to the right. The end result is shown at the right. |
Firefox 61 displaying identity information for a website |
For example, Firefox 61 on Windows requires 2 clicks before you can see that DigiCert is vouching for the CIA. First, you have to click the I in a circle, then on the half arrow pointing to the right. The end result is shown below.

Firefox 61 displaying identity information for a website
|
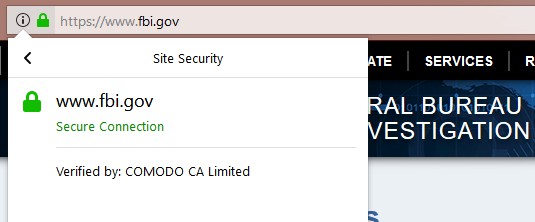
By way of comparison, the FBI does not pay for identity assurance and we see at the right, what Firefox knows about their website. Firefox says you have a secure connection to www.fbi.gov, not that you have a secure connection to the Federal Bureau of Investigation. Above, Firefox says you are securely connected to the Central Intelligence Agency. B-I-G difference. H-U-G-E difference. The message that the site was "verified" by Comodo is simply not true. Without identity assurance, there is no validation or verification to speak of. The FBI website is just like this one, which, again, is not necessarily run by someone named Michael Horowitz. |
Firefox 61 NOT displaying identity information for a website |
By way of comparison, the FBI does not pay for identity assurance and we see below, what Firefox knows about their website.

Firefox 61 NOT displaying identity information for a website
Firefox says you have a secure connection to www.fbi.gov, not that you have a secure connection to the Federal Bureau of Investigation. Above, Firefox says you are securely connected to the Central Intelligence Agency. B-I-G difference. H-U-G-E difference.
The message that the site was "verified" by Comodo is simply not true. Without identity assurance, there is no validation or verification to speak of. The FBI website is just like this one, which, again, is not necessarily run by someone named Michael Horowitz.
|
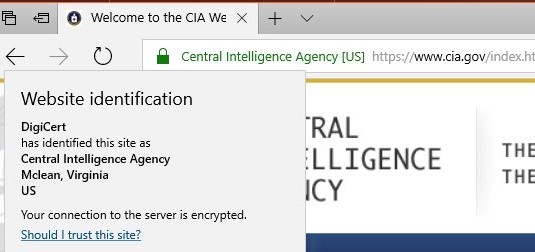
Users of the Edge browser on Windows 10 can get the site ownership information with a single click (shown at right), on either the green lock or the company name. |
 1 click with Edge on Windows 10 |
Users of the Edge browser on Windows 10 can get the site ownership information with a single click (shown below), on either the green lock or the company name.

1 click with Edge on Windows 10
|
In terms of burying information, Chrome is the worst. As seen here at the right, two clicks with version 67 on Windows gets you less information than the other browsers, and more technobabble to boot. The certificate file is intended for purpose 2.16.840.1.114412.2.1. Got that? |
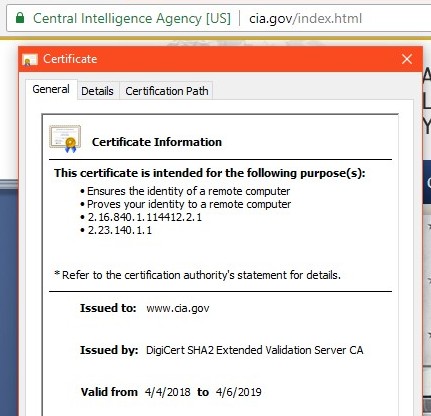 Two clicks with Chrome 67 gets you here |
In terms of burying information, Chrome is the worst. As seen below, two clicks with version 67 on Windows gets you less information than the other browsers, and more technobabble to boot. The certificate file is intended for purpose 2.16.840.1.114412.2.1. Got that?

Two clicks with Chrome 67 gets you here
But Firefox, on Windows at least, has a trick up its sleeve. Hover the mouse over "Central Intelligence Agency" and up pops a notice that DigiCert verified the site. No clicks needed at all. |
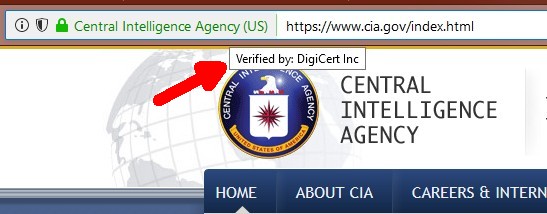
Firefox 61 displays the name of the vouching Certificate Authority when hovering the mouse over the website owner's name |
But Firefox, on Windows at least, has a trick up its sleeve. Hover the mouse over "Central Intelligence Agency" and up pops a notice that DigiCert verified the site. No clicks needed at all.
 Firefox 61 displays the name of the vouching Certificate Authority
Firefox 61 displays the name of the vouching Certificate Authority
when hovering the mouse over the website owner's name
I don't know when this feature was introduced to Firefox, clearly I missed the memo. It's a great little feature though, as it makes verifying the owner of a website simpler and faster. Of course this only works with websites that have actually had their identity verified.
The terminology describing the two types of "secure" websites, is not what I have been using here. Sites that have no identity assurance are known as Domain Validated, or DV. This is a misnomer, they are not validated in any way, shape or form. Sites that have had their identity verified are known as Extended Validation, or EV. These terms actually refer to the two different types of certificate files issued by Certificate Authority companies.
Sadly, there really is no official term for the two types of "secure" websites, most everyone lumps them together as if they were they same. For whatever reason, the techie world has focused on encryption of in-flight data as the definition of "secure", ignoring the identity assurance.
You can see this mis-placed emphasis in the below list of websites, that do not use Extended Validation, but really should.
|
www.amazon.com www.irs.gov www.nsa.gov www.fbi.gov www.WellsFargo.com www.facebook.com www.linkedin.com www.microsoft.com |
| Websites that do NOT use identity assurance |
Firefox also does the mouse hover trick with DV websites, but this is misleading. If you hover the mouse over the green lock, it says that the site was "Verified by < some CA >". What this means is that the named Certificate Authority issued the digital certificate for the website. It does not, however, mean that any verification was done. Pays your money, gets your certificate. The only thing verified was your credit card for the charge. Now that Lets Encrypt issues DV certificates for free, there isn't even a credit card to verify.
There is clearly a pattern here - overselling DV website security. The companies that make web browsers, stretch the meaning of the word "verified". Microsoft does it too.
Finally, getting off the subject a bit, there are many companies that act as Certificate Authorities. How many are there? I don't think anyone knows, but probably over a thousand. Are they all honest and reputable? This is clearly none of our business. A few have been driven out of business for making mistakes and being sloppy, but there is no Rotten Tomatoes for Certificate Authorities. Who decides which ones are trustworthy? Mozilla (in Firefox), Microsoft (in Windows) and Apple (in their operating systems). So, on Windows for example, Chrome may trust a Certificate Authority that Firefox does not.
UPDATE HISTORY:
July 16, 2018. Added two paragraphs about Man-in-The-Middle attacks. Added the paragraph above about trusted CAs. Improved the description of the FBI's DV website. Added to the list of sites using DV certificates. Added that Firefox does the mouseover trick for DV sites too.
July 17, 2018: Minor edits
July 23, 2018: Made the page much more mobile friendly. It reformats itself when the display width is less than 600 pixels.
| | ||
| Home => A hidden Firefox feature easily verifies websites | TOP | |
| michael--at--michaelhorowitz.com | Last Updated: July 23, 2018 8 PM | ||

Copyright 2001-2025 |
Copyright 2001-2025 |