| Michael Horowitz |
Home => Spying on browser history
|
| Michael Horowitz |
Home => Spying on browser history
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
November 5, 2018
The recent news coverage of web browsers leaking your browsing history sure looks like clickbait. In an ad-supported world, clickbait makes money. But, I am not ad supported and I focus on Defensive Computing. With that in mind, I will both fill in the blanks and provide a defense.
The two stories on this topic that I ran across are below. Each author corresponded directly with the authors of the research that the stories are based on.
Summarizing the two articles:
Back in August, researchers from Stanford University and UC San Diego presented a paper on four new attacks that get at people’s browsing histories. The attacks exploit new browser features such as the CSS Paint application programming interface (API), the JavaScript bytecode cache, CSS 3D transforms and SVG fill-coloring. To some degree, Chrome, Firefox, Edge, Internet Explorer and Brave were all affected. Some of the attacks even worked on security-focused browsers such as ChromeZero, Brave, FuzzyFox and DeterFox. The worst of the attacks was based on visited-links and the CSS Paint API. It was a bug in Chrome 67 and Google fixed it back in June. The three remaining flaws are timing-side channel attacks, which makes them 'considerably less severe.' The researchers proposed a new same-origin-style policy as the ultimate fix, however, they are still researching this and it will take several months to a year to implement (assuming the browser vendors even agree with them on the solution).
MISSING
There are many web browsers and many popular operating systems; the report was far from comprehensive. The biggest omission was Apple's Safari browser which was not tested at all. Neither article mentioned that Safari was ignored. The operating systems they tested with were: Windows 10, macOS 10.10 and Ubuntu Linux. No iOS or Android. The Brave browser was only tested on macOS. FizzyFox and DeterFox were only tested on Ubuntu.
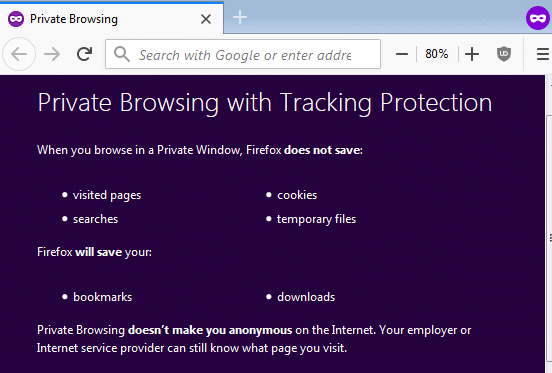
The other huge omission was private browsing mode (a.k.a incognito mode). Was this done because its such a simple defense against these new attacks? I don't know, but in a clickbait focused world, this would not surprise me. It strikes me as amazing that neither author, each of which corresponded with the researchers, thought to bring this up.
Just as obvious, and, just as missing from the discussion, are the defenses built into each browser. For example, both Firefox and Chrome let you delete history, cookies and other assorted site data. Is this a viable defense against the new attacks? None of our business.
Specifically, to clear out history, cookies, site data and cache in Firefox, bookmark this: about:preferences#privacy
The clear out history, cache, cookies and site data in Chrome, bookmark this: chrome://settings/clearBrowserData
DEFENSE
The only tested browser that was not vulnerable to any of the four attacks was the Tor Browser. Great. Neither article provided a link to it, however, or said anything about it at all.
An excellent defense against these attacks was ignored both by the press and the researchers: a Chromebook running in Guest Mode. Anyone who really cares about their browser history disappearing into thin air, is best served with a Chromebook. Arguably, the operating system isolation provided by a Chromebook makes it a better defense than the Tor browser. On the other hand, without a VPN or Tor, the Internet Service Provider can tell which websites have been visited, even when using HTTPS.
Guest mode starts out with a virgin copy of the operating system, even Chrome browser extensions are banned. When you logout of Guest mode, everything you did is thrown away. Files downloaded to the Chromebook and browser bookmarks are removed. This is an operating system thing, not a web browser thing. The only way save files from Guest mode is to write them to an external device, such as a USB flash drive.
One possible defense was mentioned in the paper, but not the articles. The paper says "Turning off Firefox's layout.css.visited links enabled configuration flag should eliminate visited link styling altogether. Not so: disabling the flag fails to block either our visited-link attacks or Paul Stone’s older one; we reported this bug to Mozilla." The researchers tested Firefox 60, so we are left wondering if this has been fixed in the current version (63) of Firefox. Such is the current state of the tech press, that neither reporter thought to ask the researchers this question.
So, this may be news, but its just as likely to be clickbait generated by a Public Relations company. My guess, is that it's clickbait. My last argument is a later article on the subject by Martin Brinkmann of gHacks.net. He writes that "All four attacks have in common that they need to specify URLs to check; none manages to retrieve a user's entire browsing history."
- - - - - - - -
The original research paper: Browser history re:visited by Michael Smith, Craig Disselkoen, Shravan Narayan, Fraser Brown and Deian Stefan.
| | ||
| Home => Spying on browser history | TOP | |
| michael--at--michaelhorowitz.com | Last Updated: November 6, 2018 2 AM | ||

Copyright 2001-2025 |
Copyright 2001-2025 |